With macOS Mojave (10.14), Apple has changed how applications can obtain access to the system resources and how to manage their permission, which slightly changes the workflow when using ISL Online products. This topic begins byshowing how the process of running ISL Online applications has changed and then continues with how to use MDM solutions to bypass the newly introduced changes. Please select the appropriate part for you:
Running ISL Online applications
Please take a look at the steps below, showing how to connect to an ISL Light session as a client, to familiarize yourself with the new workflow on your macOS Mojave.
Important: Step 3 and onward show steps that are specific to macOS Mojave. Those steps are equivalent for any other ISL Online product when running or installing a new application, such as ISL AlwaysOn, ISL Groop and others.
Step 1
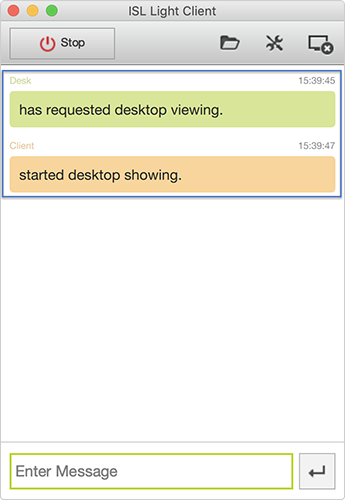
Launch ISL Light Client.
Note: ISL Light Client is automatically download when you enter the session code at www.islonline.net
Step 2
Wait until you are connected to the session. Operator will be able to see your screen but will be unable to control your computer.
Step 3
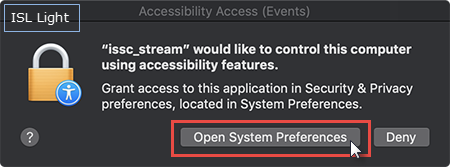
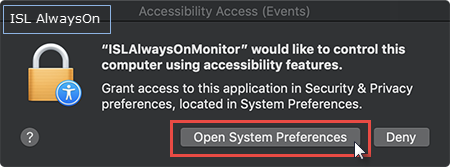
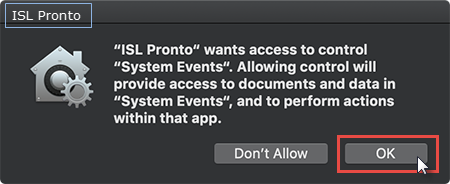
Info: The dialog boxes above are new in macOS Mojave and differ for each ISL Online product. It tells you which application requested access to which resource.
Important: Dialog in Step 3 is launched at runtime, as soon as the Operator requests control or performs any action which can be translated to your computer e.g. moves the mouse, presses keyboard key...
Important: Dialog in Step 3 has to be approved only once as your device will remember the choice in the Security & Privacy settings. Please note that you will need the administrative password in order to edit the System Preferences.
In the dialog box that appears click on "Open System Preference" to manage the application permissions.
Step 4
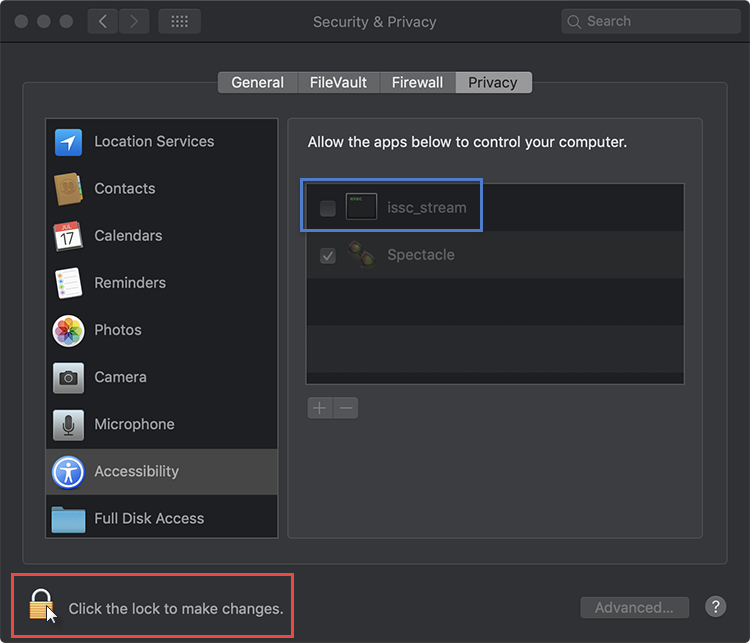
To change permissions click on the Lock icon and enter administrative password.
Step 5
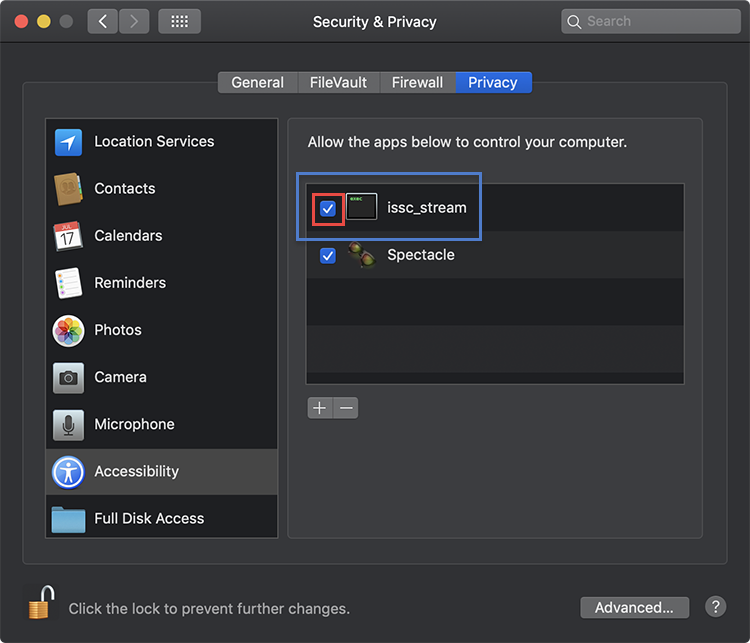
Tick the box next to "issc_stream" to allow ISL Light to control your computer. As soon as you tick the box the operator will be able to control your device.
Note: You can uncheck this box at any time and revoke the permissions. If you do this during a session the operator will immediately loose control of your device.
Using User Approved MDM solutions
Important: Due to the way ISL Online applications are designed it is currently only possible to create a privacy policy exception for ISL AlwaysOn trough MDM system. Other applications are currently in the process of supporting MDM and examples will be posted here as soon as functionality is enabled for them as well.
Note: MDM solutions are primarily meant to be used by system administrators who are responsible for setting up and configuring a number of machines.
With Apple's MDM solutions you can, among other things, pre-approve certain applications to access system resources without the user having to approve a checkbox every time the application requests access to a new resource.
There are many different ways of MDM tools on the market which help you configure your devices, however in all cases you will have to provide the following information in order to create a privacy policy exception:
- Identifier - The unique identifying value for the binary or service. For applications, specify the bundle ID - it is also possible to use the installation path for supporting binaries.
-
Code Requirement - This is a unique string based upon the developer certificate which was used to sign the Identifier (binary or bundle ID). You can obtain this value by running the following command in Terminal.app:
codesign --display -r - /path/to/app/binary
- Static Code Validation - Some applications might intentionally make changes to themselves in memory. If you set Static Code Validation to True, macOS checks only the Code Requirement of the files on disk and not the application loaded in memory. Generally speaking, use this option as a last resort if you are absolutely sure the Code Requirement and Identifier are correct.
- Accessibility Privacy preferences - Accessibility section of the macOS Mojave Security & Privacy panel allows apps to control your Mac in various ways. Certain ISL AlwaysOn and ISL Light/ISL Light Client apps and binaries need permission to gain access to Accessibility system services.
Please refer to the example for the relevant ISL Online product below:
ISL AlwaysOn
Binary ISLAlwaysOnMonitor requests access when session is established using ISL AlwaysOn. Binary issc_daemon requests access when restart and resume functionality is in use (e.g. restart of computer).
ISL AlwaysOn monitor
Path:
"/Library/Application Support/ISLAlwaysOn/ISLAlwaysOnMonitor"
Note: By using certain customization options it is possible that the path on your device is slightly different than in the example above. In that case please modify it accordingly.
Code Requirement:
identifier "com.islonline.islalwayson.monitor" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GP5P6H7RRF
Static Code Validation:
No
ISL AlwaysOn issc_daemon
Path:
"/Library/Application Support/ISLAlwaysOn/issc_daemon"
Note: By using certain customization options it is possible that the path on your device is slightly different than in the example above. In that case please modify it accordingly.
Code Requirement:
identifier "com.islonline.islalwayson.issc_daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GP5P6H7RRF
Static Code Validation:
No
ISL Light and ISL Light Client
Application bundle issc_stream requests access when session is established using run once mode of ISL Light or ISL Light Client. Application bundle isllight requests access when session is established using installed ISL Light. Binary issc_daemon requests access when restart and resume functionality is in use (e.g. restart of computer).
issc_stream
Bundle Id:
"com.islonline.isllight.issc_stream"
Code Requirement:
identifier "com.islonline.isllight.issc_stream" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GP5P6H7RRF
Static Code Validation:
No
isllight
Bundle Id:
"com.islonline.isllight.main"
Code Requirement:
identifier "com.islonline.isllight.main" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GP5P6H7RRF
Static Code Validation:
No
isllight_launch
Bundle Id:
"com.islonline.isllight.launch"
Code Requirement:
(anchor apple generic and certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GP5P6H7RRF) and identifier "com.islonline.isllight.isllight"
Static Code Validation:
No
issc_daemon
Path:
"/Library/Application Support/ISL Online/ISSC Daemon/issc_daemon"
Note: By using certain customization options it is possible that the path on your device is slightly different than in the example above. In that case please modify it accordingly.
Code Requirement:
identifier "com.islonline.isllight.issc_daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GP5P6H7RRF
Static Code Validation:
No